nmap - how to scan hosts of networks for open ports
Written by Guillermo Garron
Date: 2008-01-02 10:36:30 00:00
Introduction
nmap is a wonderful tool specially for debugging, there are lots of times when you need to know if a port is open in a server, or maybe blocked by a firewall, or just to test your iptables rules.
Here we will learn how to use it at the command line, and using its GUI front end, nmapFE and Knmap.
Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
—-The man page
Command Line
Nmap has lots of options, so we are going to focus on only some of them.
sudo nmap -sS -O 127.0.0.1- -sS
- TCP SYN scan
- -O
- Enable Operating System detection
sudo nmap -sU 127.0.0.1- -sU
- UDP ports scan
sudo nmap -sS -O -p 20-25 127.0.0.1- -sS
- TCP SYN scan
- -p 20-25
- Scan on ports 20 to 25
sudo nmap -sS -F 127.0.0.1- -sS
- TCP SYN scan
- -F
- Fast (limited port) scan
Graphical interfaces
This is one of its front ends to install it run:
For Fedora / Centos
sudo yum install nmap nmap-frontendFor Debian / Ubuntu
sudo aptitude install nmapfe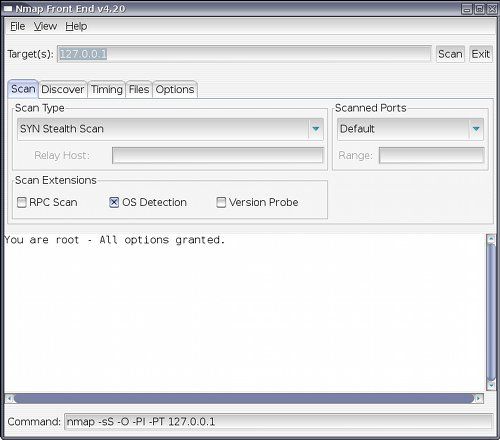
On target you put the IP or IPs you want to scan, select the scan type, if you want TCP SYN, UDP, Connect scan, or other, the most used are SYN and UDP if you want to scan for UDP ports. Also select the scanned ports, you can scan the default ones, All, fast (only the ports in nmap-services file).
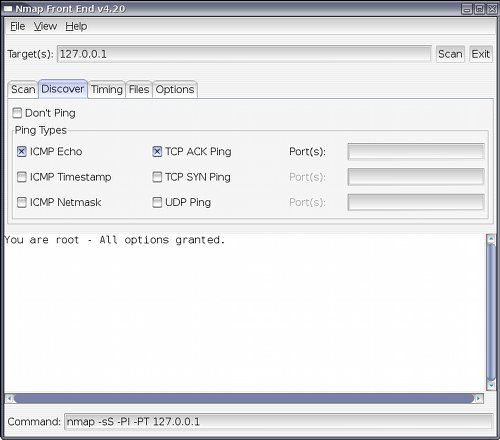
Select if you want to use the discovery option, if you want to ping and which type of ping you want to use to discover network nodes if you have specified an IP range to scan.
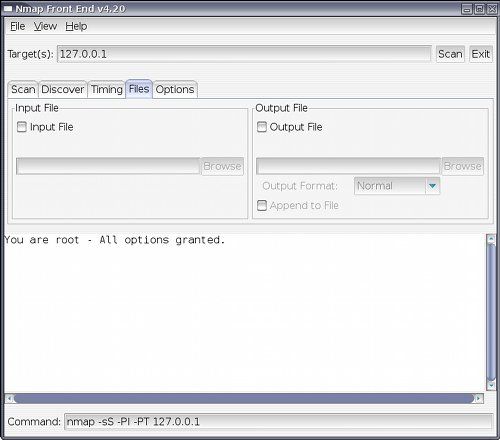
Useful if you want to send the output to a file.
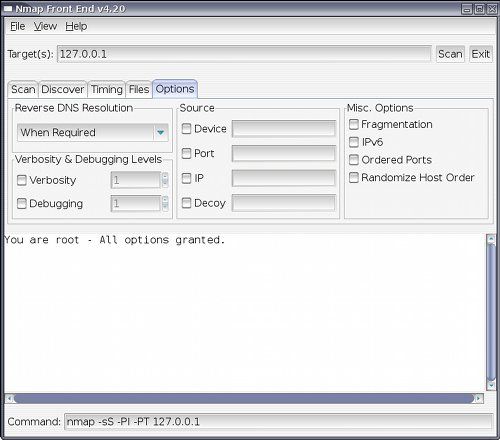
Lots of other tools, if you want you can enable verbosity of debugging, and if you want IPv6 support.
KDE Nmap (knmap)
To install it
For Fedora download the rpm here
then run:
sudo rpm -ivh [downloaded package]For Debian or Ubuntu do this:
sudo aptitude install knmap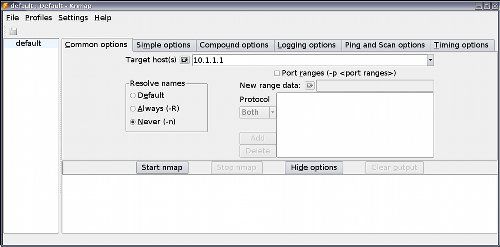
Its interface has divided the options in a very convenient way, in the common options you will see the target IPs, the port range and if you want it to resolve names.
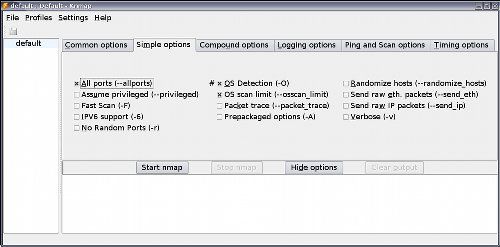
Here you select if you want to scan all ports, perform a fast scan, IPv6 support, Operating System detection, verbose, and other options.
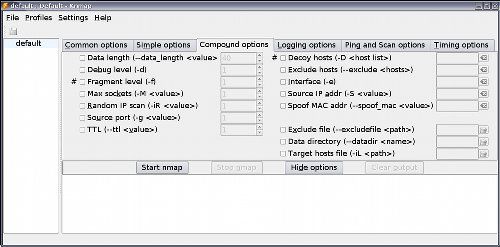
In compound options, you will find a lot more options to play with, you can select which interface to use, which IP, and even if you want to spoof your Mac address!
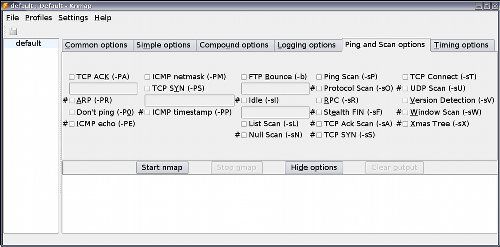
Ping and scan options is like the discover and the scan tabs of nmapFE together.
Conclusion
Nmap is a must have tool for network and security administrators, also the GUI front ends are good and easy ways to use them, and also to learn how to use them, because you can discover new applications, and with nmapFE you can see the command that is going to be executed, another good point for knmap is that it has the possibility to save profiles, with all the options you have enabled, so your next scan is easier.